DeepSeek database leaked online: open data gave full control of the system

Cybersecurity company Wiz has discovered an open DeepSeek database containing chat history, API keys and other sensitive information. Moreover, the vulnerability allowed full control of the system without the need for authentication.
.
What happened?
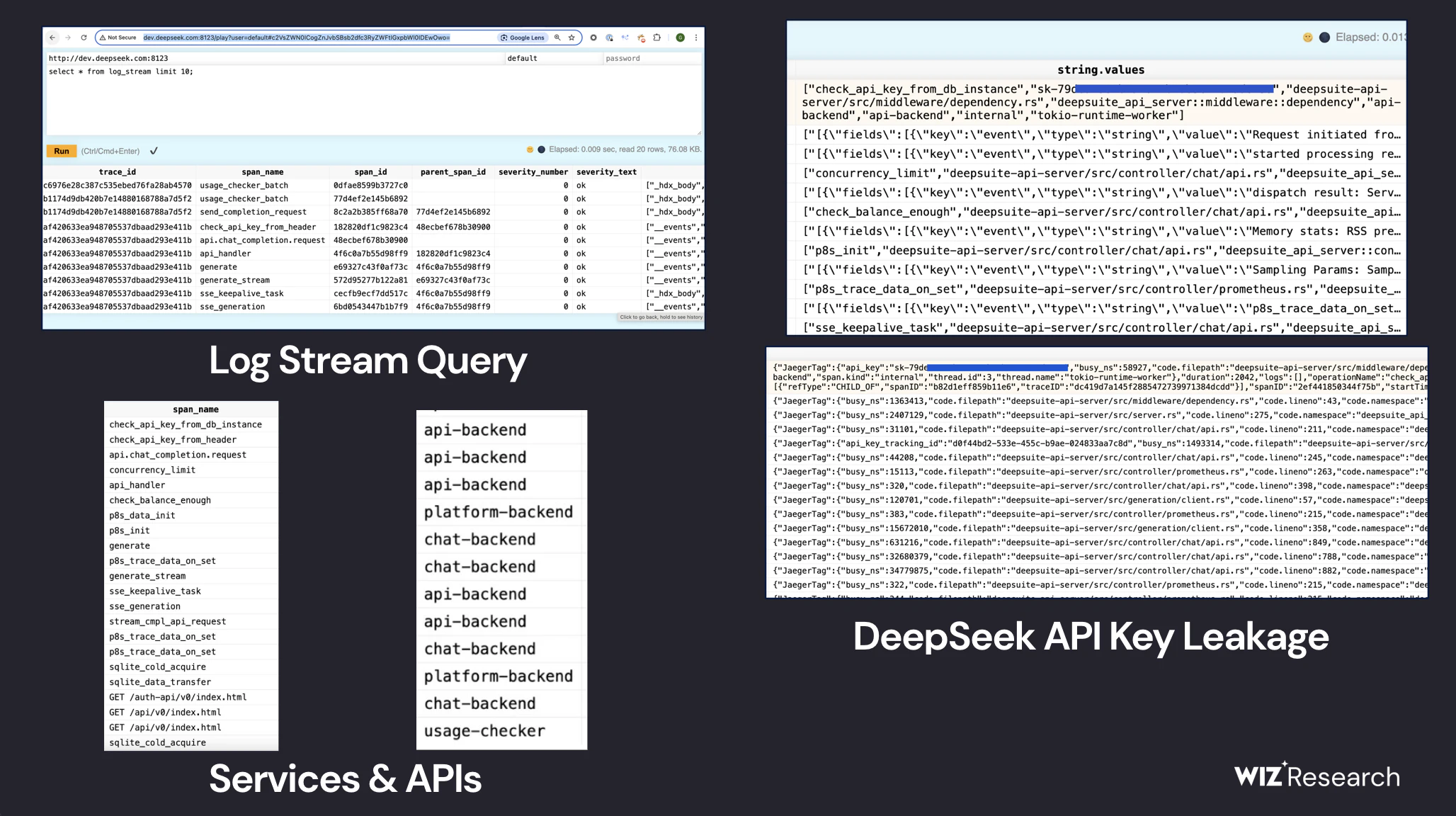
Wiz investigators said they found an insecure ClickHouse database linked to DeepSeek in just a few minutes. This database contained over a million lines of logs, including internal data, chat history, API keys, and operational information. The most serious threat was that any user could gain administrative privileges on the DeepSeek system without logging in or bypassing security mechanisms.
The most serious threat was that any user could gain administrative privileges on DeepSeek without logging in or bypassing security mechanisms.
Wiz experts clarified that ClickHouse is an open-source database management system developed by Yandex and widely used for real-time analytics, log storage and working with large data sets.
How was the vulnerability discovered?
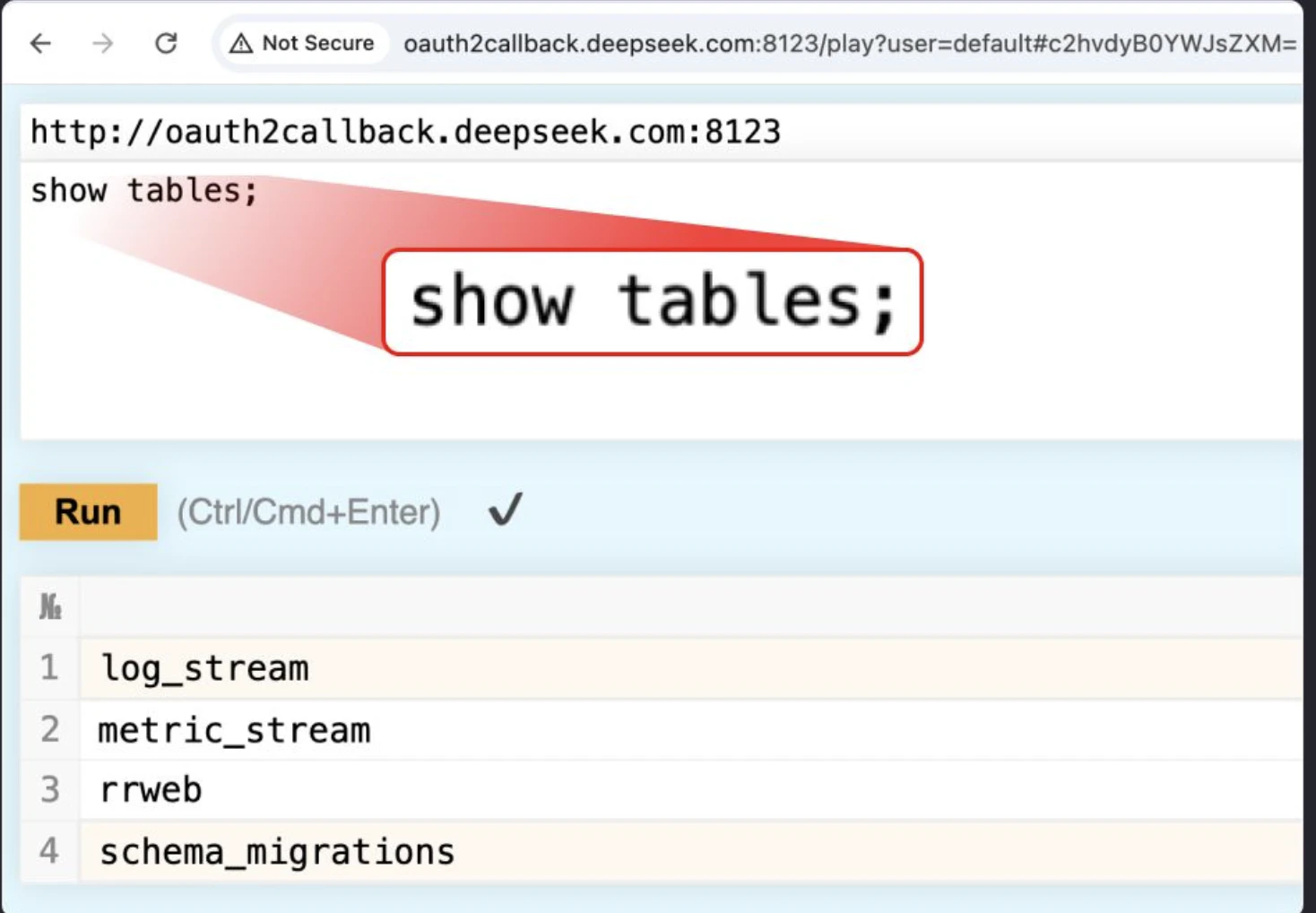
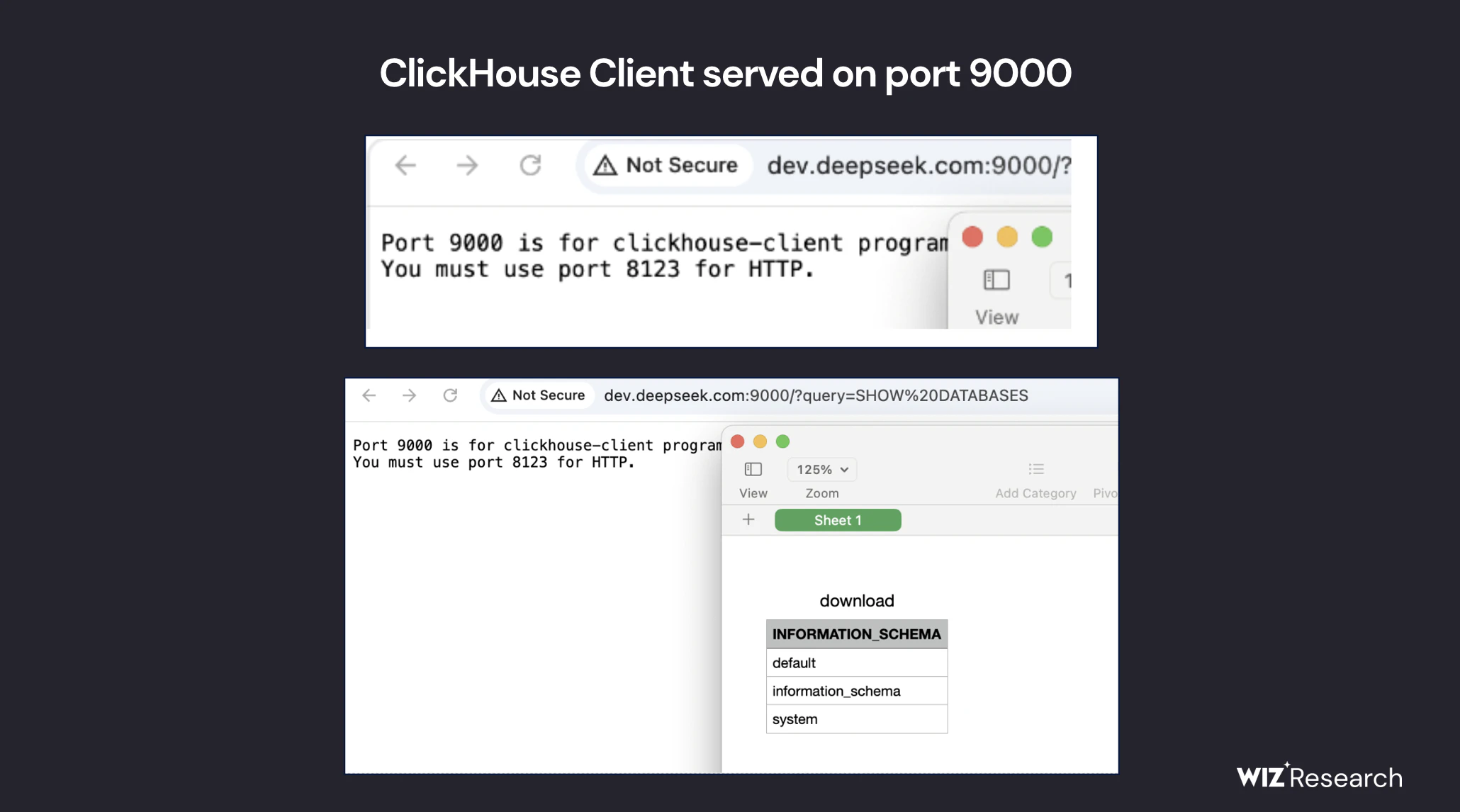
The Wiz team began investigating DeepSeek’s external security and identified about 30 of the company’s public subdomains. However, the most critical problem was discovered when analyzing the public ports. Two of them (8123 and 9000) led to a fully accessible ClickHouse base that did not require authentication.
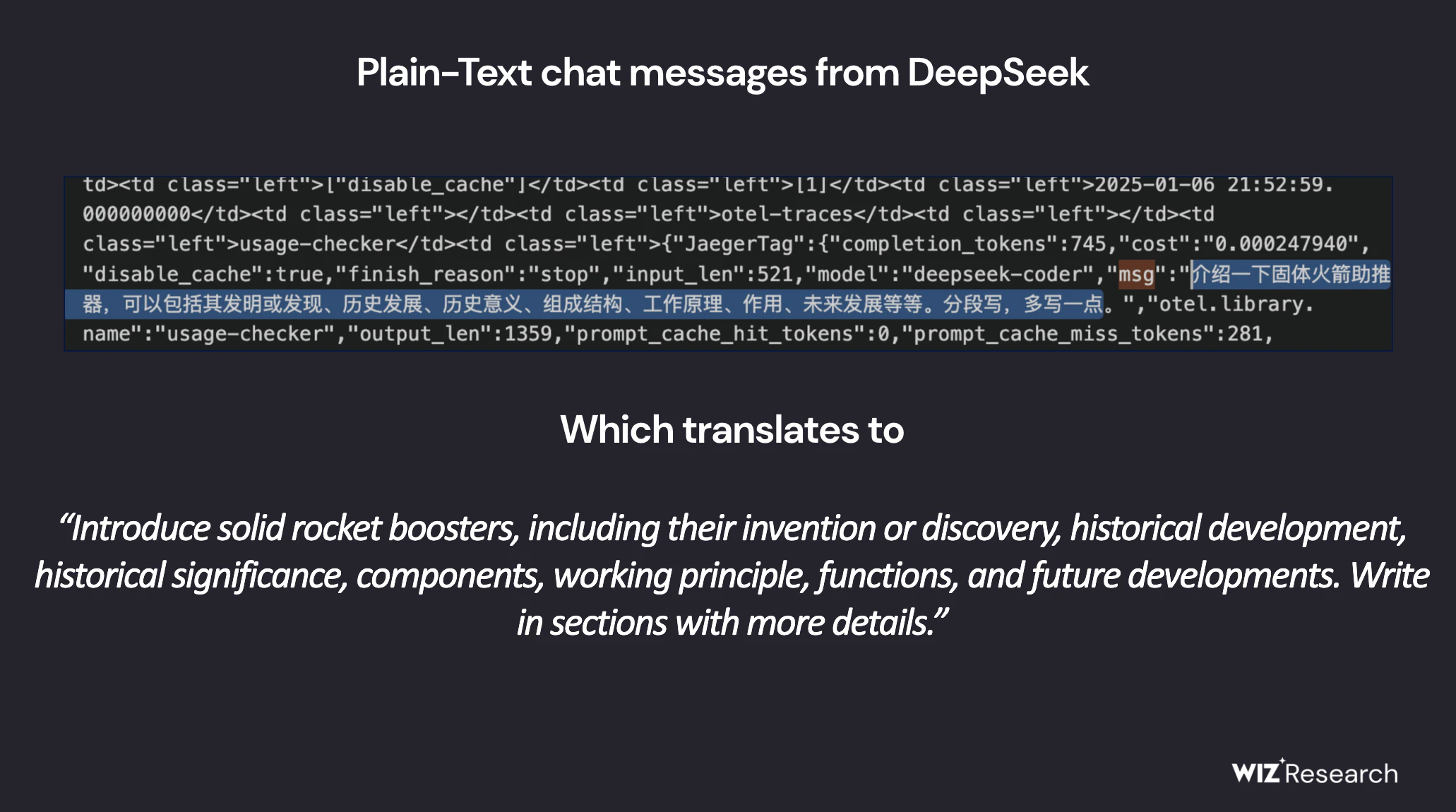
Of the tables discovered, the one that drew particular attention was log_stream, which contained more than a million records, including:
- temporary log labels from January 2025;
- links to DeepSeek’s internal APIs;
- text logs with chat history, API keys and system metadata;
- data about the services that generated these logs;
What’s more, the vulnerability allowed not only reading data, but also executing SQL queries, potentially retrieving files and other critical information.
What risks did this create?”
This leak posed a serious threat not only to DeepSeek itself, but also to its users. Attackers could access sensitive information, including chats and internal system data, as well as potentially extract passwords and files from the company’s servers.
An attacker could access sensitive information, including chats and internal system data, and potentially extract passwords and files from the company’s servers.
How did DeepSeek fix the problem?”
.
After discovery, Wiz promptly notified DeepSeek of the problem, and the company quickly closed the vulnerability. However, this case highlights a global problem: the rapid development of AI companies is often accompanied by insufficient security.
After the problem was discovered, Wiz promptly notified DeepSeek, and the company quickly closed the vulnerability.
Conclusions
This leak demonstrates that the main threats to AI companies are not only from outside attacks, but also from underlying infrastructure defense issues. AI and big data organizations need to pay more attention to cybersecurity, especially in protecting user data.